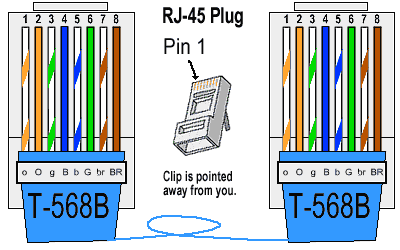
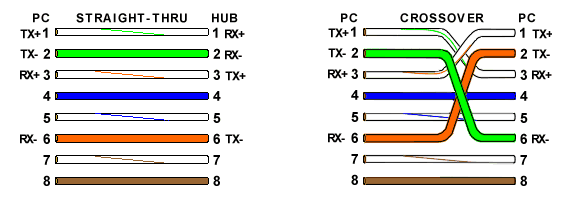
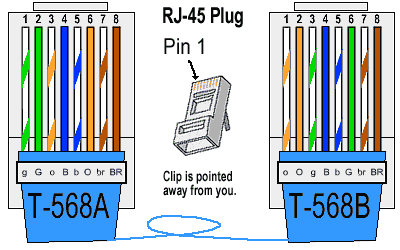
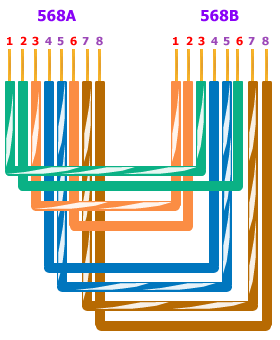
Below is the wiring diagram of both the Straight Through and Cross-Over cables:
Straight Through Cable

Cross-Over Through Cable
RJ45 Clip ( Registered Jack 45 Clip)
| | An connecter used to connect 4 pair ( 8 wire) Unshielded Twisted Pair (UTP) cable. RJ-45 connectors look similar to the RJ-11 connectors used for connecting telephone equipment, but the RJ45 somewhat wider than RJ11. The tool used to connect RJ45 with Unshielded Twisted Pair (UTP) cable, is called ' Crimping tool'
There are lot of crimping tools available with RJ45+RJ11 support. We can make two types Unshielded Twisted Pair UTP network cables by changing the wire combinations.
Crossover Cable Crossover cable can be used to directly connect two computers to each other without the use of a hub or switch in networking. It also used to connect two hubs or switch without the use of an uplink port in LAN to expand the network.
How to make Crossover Ethernet Cable:
That should be it, if your cable doesn't turn out, look closely at each end and see if you can find the problem. Usually a wire ended up in the wrong place or more commonly, one of the wires didn't extend to the front of the RJ45 connector and is making no, or poor contact. If you see a mistake or problem, cut the end off and start again. Straight Through Cable Straight-through cables are used for a variety of connections.
Straight-through: A straight-through network cable is just what the name implies, a cable that passes data straight through from one end to another. It can also be used to directly connect like devices (e.g., two hubs or two switches) if the cable is plugged into an uplink port on one (but not both) of the devices. Crossover cable is used to connect two like devices without the use of an uplink port. How to make Straight Through Ethernet Cable: Follow the same steps in Cross cable method, except aligning the colored wires. |